About Cybersecurity Awareness Month
Cybersecurity Awareness Month (October) is a national initiative that highlights essential actions to reduce cybersecurity risks. This year’s theme is Building a Cyber Strong America, highlighting the need to strengthen the country’s infrastructure against cyber threats, ensuring resilience and security.
Cybersecurity is more than just an IT concern — it’s a cornerstone of national security and organizational resilience. Critical infrastructure spans everything from utilities and transportation to hospitals, schools, and emergency services. Small and medium-sized businesses also play a vital role — whether as suppliers, contractors, vendors, or manufacturers, they help sustain these essential systems. Disruptions to these networks have immediate and widespread consequences. Safeguarding them begins with the daily online actions of every individual.
 What is the CIA Triad? How does this apply to me?
What is the CIA Triad? How does this apply to me?
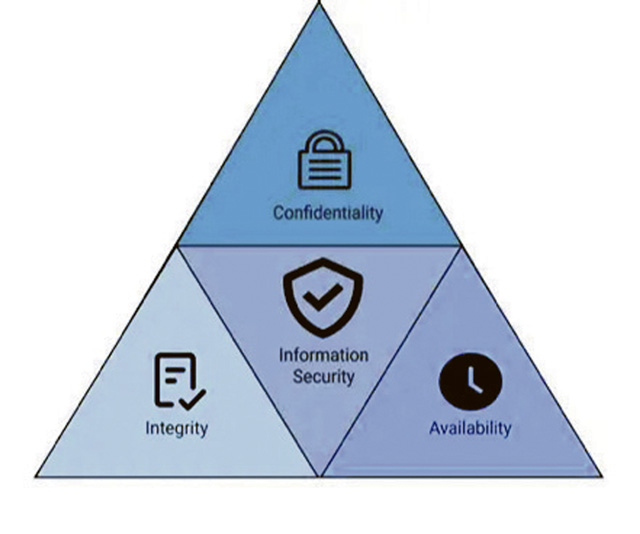
Cybersecurity has three core goals: Confidentiality, integrity, and availability. These goals are signified by a model called the CIA Triad. This model is used to guide an organization’s security principles and practices. Each element, each goal, and each best practice, is essential to achieving a high degree of security certainty.
Confidentiality: Confidentiality prevents unauthorized disclosure of information. It keeps sensitive information secret.
Integrity: Integrity prevents the unauthorized alteration or modification of information systems. It keeps information safe from intentional or accidental changes.
Availability: Availability ensures authorized users can access information and systems when they need them.
When it comes to end-user security, these core goals work together to protect sensitive data, ensure its accuracy, and secure the systems that enable access — achieved through a comprehensive strategy that includes strong passwords, multi-factor authentication (MFA), scam detection and reporting tools, and a resilient defense against ever-evolving cyber threats.
The reason why all of this matters:
In today’s world, threats to confidentiality, integrity and availability are ever present. Currently, the rise of artificial intelligence, sophisticated ransomware operations, and evolving geopolitical tensions are dramatically reshaping the cybersecurity landscape in 2025. AI-driven attacks have increased by 67 percent compared to 2024. Threat actors leverage machine learning algorithms to bypass traditional security measures, automate reconnaissance, and craft convincingly personalized phishing campaigns. Ransomware will likely remain a dominant threat in 2025, with attacks across North America increasing by 8 percent over the last year. The most concerning development is the proliferation of models, which drastically lower the technical barrier for would-be attackers and researchers have identified a troubling trend in RaaS operations, noting that many groups now employ double and triple extortion tactics (CISO Advisory, 2025).
Credential theft has reached staggering levels, with billions of items stolen during 2024, a significant increase year-over-year. More alarming still, most of these credentials were taken through malware attacks. This trend has accelerated in 2025 as threat actors employ multiple malwares installed through single instances, maximizing their harvest from each successful breach. The stolen information enables subsequent attacks, particularly by ransomware operators who use harvested credentials to gain initial access. With cybercrime expected to cost over $10 trillion globally in 2025, the stakes are extremely high for public and public and private organizations to adapt their security postures to this rapidly changing threat landscape.
What can I do?
Reducing risk is also known as risk mitigation. Risk mitigation reduces the chances that a threat will exploit a vulnerability or the impact that the risk will have on the organization if it does occur. You reduce risks by taking the initiative to actively exercise best security practices. A comprehensive security management strategy combines strong passwords, password managers, multi-factor authentication, tools for recognizing and reporting scams, and creating a resilient defense against ever-evolving cyber threats.
How do I implement strong passwords, password managers, multi-factor authentication, tools for recognizing and reporting scams, and a resilient defense against ever-evolving cyber threats?
We’ll break down each cybersecurity practice — like strong passwords, MFA, and scam detection — with clear guidance to help you stay secure in today’s fast-changing digital world.
 Multi-Factor Authentication:
Multi-Factor Authentication:
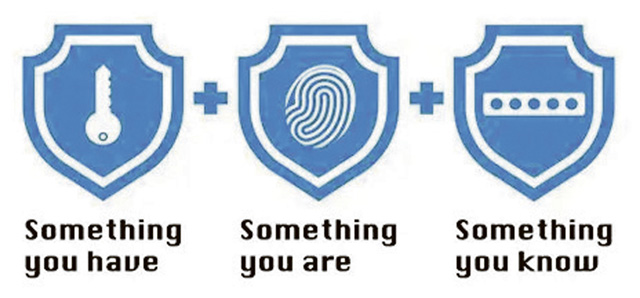
MFA provides an extra layer of security to protect organizations’ sensitive data and systems. The implementation of MFA requires users to authenticate their identity using distinct authentication methods. Those authentication methods can include something you know (password), something you have (smart card), and/or something you are (fingerprints). By requiring at least two of these categories, MFA makes it more challenging for attackers to access data and systems.
Something you know: A password and pin (these two put together are still ONLY one MFA)
Something you have: A phone, hardware token, or smart card, CAC
Something you are: Biometrics like a fingerprint
For example, before I can gain access to my computer to operate on the government’s network I need something I know and something I have (PIN + CAC).
Use MFA as often as possible as it combines all principles of the CIA triad to ensure security.
Strong passwords:
Creating a strong password that you can easily remember sounds simple enough, however is often easier said than done. While newer technologies emerge and passkeys become more commonplace, most of us still use passwords for a multitude of accounts and profiles. When generating a new password, if you just used upper case and lowercase letters, there are 53 trillion possible combinations. Mix in digits to the password such as (0-9) now there are 218 trillion combinations. Add special characters which are 32 symbols such as (!@#$%^&*()-_=+ etc.) now you have 6.1 quadrillion combinations. The more complex your password is, the more difficult it becomes to crack. The trouble with stronger passwords is that they are also more difficult to remember as security and convenience are two concepts consistently at odds. As a rule of thumb, a 16-character password with 2 uppercase, two lowercase, and 2 special characters will ensure a password that is significantly more difficult to crack.
A strong alternative to this is to generate a passphrase. A passphrase is a longer sequence of words, characters, or numbers used to authenticate a user. Unlike a password, which is typically a short string of letters, numbers, and symbols, a passphrase is often a longer string-usually a series of words or a sentence-that forms a more complex and secure piece of information for access control. A passphrase is typically longer than a password and if randomized, can introduce a much stronger barrier to cracking (CISO Advisory, 2025).
If using a traditional password, completely randomizing your passwords while also changing your password every 6-12 months will keep hackers at bay.
Using a password manager
One method to track and manage passwords is the use of a password manager.
To put it simply a password manager is a secure digital tool that stores and organizes your passwords in an encrypted digital vault. You only need to remember one master password to access your digital vault. The password manager automatically fills in login credentials for website and apps, making your online experience both safer and more convenient.
Recognizing and reporting scams:
Scams take many forms — emails, text messages, phone calls, websites, and even social media. Here are some key red flags to watch for:
- Urgency or fear tactics: Messages that say, “ACT NOW!!!” “Your account will be closed” etc.
- Too good to be true: Promises of free money, prizes, or miracle cures.
- Unusual requests: Ask for gift cards, wire transfers, or cryptocurrency payments.
- Suspicious links or attachments: Hover over links to see the URL. IF ODD, DON’T CLICK!
Poor grammar or generic greetings: Broken English and vague intros like, “Dear Customer”
The Federal Trade Commission provides a central hub for reporting fraud, scams, and deceptive business practices. This platform is called ReportFraud.ftc.gov. It allows individuals to submit complaints and helps authorities track and respond to emerging threats. USA.gov (Scams and Fraud) can help you find the right agency based on the type of scam and where it happened. FBI.gov is the go-to place for reporting cyber-enabled crimes like phishing, ransomware, and online fraud. Here in Germany, U.S. citizens can go through the U.S. Embassy & Consulates in Germany to report foreign scammers. Remember, do not try to confront the scammer, tell them that you have found them out, or investigate them yourself. Replying may only encourage more scam messages.
 Software updates:
Software updates:
Software updates matter! They uphold a resilient defense against ever-evolving cyber threats. When software is updated, it often includes a patch for newly discovered security flaws. With that in mind, it is also always best practice to verify where you are getting your software updates from.
Sophisticated scams can introduce what appear to be legitimate updates which are installing back-doors into your system or device. To combat this, you can take the following steps.
- Ensure all client devices — regardless of operating system — are updated with the latest security patches and configurations.
- Enable automatic updates on all systems and devices.
- Never download updates from emails, pop-ups, or unofficial websites.
Summary:
Cybersecurity isn’t just a technical issue — it’s a personal responsibility that starts with everyday choices. By embracing strong passwords, smart tools, and vigilant habits, we become the first line of defense against evolving threats. Stay sharp, stay secure, and remember: your awareness is the most powerful shield in the digital world.


